Archive
HECA MENLI 1 W DME arc
Now that was a beautiful & perfect DME arc, approaching rwy 05R in HECA with an Airbus 380-800 in X-Plane 10.
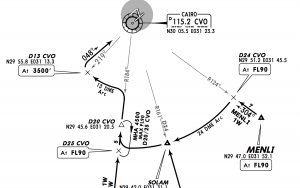
DME arc according to the chart
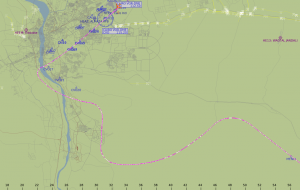
Training flight record in X-Plane 10 (pink line)
Here’s the full flight
DSA 2670-1
– ————————————————————————-
Debian Security Advisory DSA-2670-1 security@debian.org
http://www.debian.org/security/ Yves-Alexis Perez
May 11, 2012 http://www.debian.org/security/faq
– ————————————————————————-Package : wordpress
Vulnerability : several
Problem type : remote
Debian-specific: no
CVE ID : CVE-2011-3122 CVE-2011-3125 CVE-2011-3126 CVE-2011-3127
CVE-2011-3128 CVE-2011-3129 CVE-2011-3130 CVE-2011-4956
CVE-2011-4957 CVE-2012-2399 CVE-2012-2400 CVE-2012-2401
CVE-2012-2402 CVE-2012-2403 CVE-2012-2404
Debian Bug : 670124Several vulnerabilities were identified in WordPress, a web blogging
tool. As the CVEs were allocated from releases announcements and
specific fixes are usually not identified, it has been decided to
upgrade the WordPress package to the latest upstream version instead
of backporting the patches.This means extra care should be taken when upgrading, especially when
using third-party plugins or themes, since compatibility may have been
impacted along the way. We recommend that users check their install
before doing the upgrade.For the stable distribution (squeeze), those problems have been fixed in
version 3.3.2+dfsg-1~squeeze1.For the testing distribution (wheezy) and the unstable distribution
(sid), those problems have been fixed in version 3.3.2+dfsg-1.We recommend that you upgrade your wordpress packages.
Further information about Debian Security Advisories, how to apply
these updates to your system and frequently asked questions can be
found at: http://www.debian.org/security/Mailing list: debian-security-announce@lists.debian.org
… any suggestions?
Skeip straitjackets users
 Skeip is straitjackening its users who are not allowed to run a jailbreaked device. – One more reason to use Free software!
Skeip is straitjackening its users who are not allowed to run a jailbreaked device. – One more reason to use Free software!
Y R U NO ON JBBR?!
Keeping GeoIP database updated
Here’s a simple script to install on a server to keep the GeoIP db updated.
Source code for file (e.g.) get_latest_GeoIP.sh
#!/bin/bash
# getting the latest GeoLiteCity database from maxmind
host=$(hostname -s)
stamp=`date +"%m%Y"` # getting current month & year for GeoLiteCity filename
if [ -f "/usr/share/GeoIP/GeoLiteCity_"$stamp".dat" ]; then
last=`date -r /usr/share/GeoIP/GeoLiteCity_"$stamp".dat +"%m%Y"`
else
last=0000
fi
if [ ! -f "/usr/share/GeoIP/GeoLiteCity_"$stamp".dat" ] || [ "$stamp" != "$last" ]; then # if current file doesn't exist or current file wasn't modified in the current month
wget -O "/usr/share/GeoIP/GeoLiteCity.dat.gz" http://geolite.maxmind.com/download/geoip/database/GeoLiteCity.dat.gz
if [ ! -s "/usr/share/GeoIP/GeoLiteCity.dat.gz" ]; then
rm /usr/share/GeoIP/GeoLiteCity.dat.gz
exit 1
else
rm /usr/share/GeoIP/GeoLiteCity.dat
gunzip /usr/share/GeoIP/GeoLiteCity.dat.gz
if [ -f "/usr/share/GeoIP/GeoLiteCity_"$stamp".dat" ]; then
rm /usr/share/GeoIP/GeoLiteCity_"$stamp".dat
fi
mv /usr/share/GeoIP/GeoLiteCity.dat "/usr/share/GeoIP/GeoLiteCity_"$stamp".dat"
ln -s "/usr/share/GeoIP/GeoLiteCity_"$stamp".dat" /usr/share/GeoIP/GeoLiteCity.dat
echo "Report: GeoIP Database "$stamp" has been updated on "$host". - Enjoy!"
fi
fi
exit
… now just install a cronjob, that checks withn the first days of the month, whether there is a fresh GeoIP db to fetch.
22 3 1-10 * * ~/get_latest_GeoIP.sh > /dev/null 2>&1
Skeip babbling user’s IP
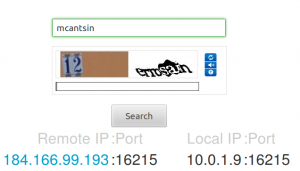 It’s a feature, not a bug!! 😛
It’s a feature, not a bug!! 😛
Skeip IP finder (See Screenshot)
For further reading: Skype divulges user IP addresses
Glauben
Glauben ist etwas für Menschen die nicht wissen.
Die Fledermaus
Operette für vier Schauspieler und zwei DJ’s
Ein Stück von “theater konstellationen” frei nach Johann Strauss
Langeweile kann tödlich sein. Vor Allem in einer Gesellschaft, in der es per Gesetz verboten ist, sich zu langweilen. Die Strafen sind hart: Wer auf einer Party beim Gähnen erwischt wird, wandert ins Gefängnis. Wer Anderen den Spass verdirbt, wandert in die Todeszelle.

