Violations on users PIM
While Apple Computers decided to violate users rights once more, ceasing the capability to synchronise PIM (personal information management) data locally with OS X Mavericks 10.9 (argueing they should store their data in their iCloud. – Bwahahahaha!1!!) there are too many PIM solutions for GNU/Linux users, whereas none of them are really feasible for users who want to switch to Free Software.
While many complain that there are too few GNU/Linux Desktop users and Linus Torvalds claims this to be his “personal failure” the GNU/Linux community fails to offer a seamless integration of GUI (graphical user interface) PIM into their OS. (Which is really sad, as fiddling around with SoGo-connector, lightning etc. does not offer a sustainable solution…)
So here is my solution:
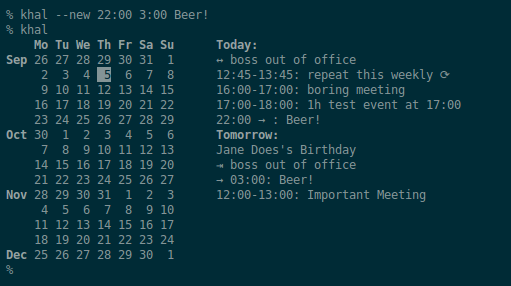
Get DAViCal, install it on your server and get mutt, pycarddav and khal for your desktop(s), get a Jolla and you will have a beautiful and seamless PIM solution using the “good olde command line”.