Swiss Aero space under military surveillance
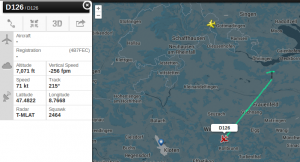
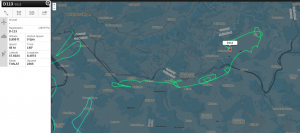
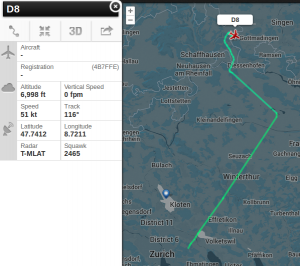
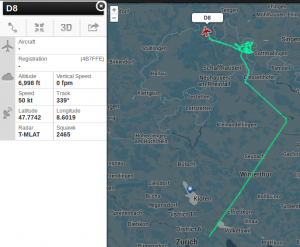
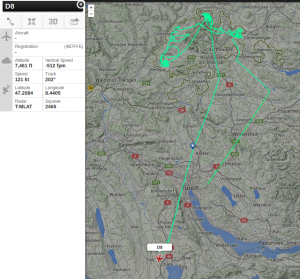
Since monday night (18th August 2014) ADS95 Ranger Drones are flying within TMA (traffic manoevering area) LSZH (ICAO code for ZRH, Zurich), using callsigns such as FOCUS1 and FOCUS2, seemingly equipped with ADS-B, as they are now visible on Flightradar24 and other platforms.
(Note that the stupid military operator does not know that the transition level for TMA LSZH is FL70 and therefore asks for clearance for FL60 instead of 6000ft!)
The virtual pilot navigating the drone applied for respective flightplans (LSME ZUE ROMIR KLO LSME) with Skyguide, – according to my call with them, – from LSME (Emmen) to LSME, without further explanation, intention nor defined route.
As there is no comprehensible reason, such as WEF Davos or Swiss political revolution for such an operation, I hereby propose to install a selfshot system equipped with ADS-B receiver to take these surveillance systems down smash into ground!
Further I should say that the Swiss Military in Emmen was very surprised by my call (01:30 a.m. CEST) to learn hat the drones are visible for anyone, as they seemingly are equipped with ADS-B. – Grotesque!
The responsible person for the operation told me on the phone that the Ranger Drones by Ruag have been in a mission to secure the Swiss-Germano border for the whole week already.
[Update 0130 UTC]
Mr. Röthlisberger, military police sergeant from VBS, was not only surprised to learn that the drones are visible for anyone through secondary radar, but, – surprisingly, – was not aware that drones from the swiss military were in operation at all, though his office is in charge for military operations within swiss aerospace!
NOTAM:
RUAG AD95 drones by Swiss Military use callsigns FOCUS1, FOCUS2 etc., whereas the registration numbers vary from D-113, D-138, D-8 etc. (*not* HB-XXX, as usual for registered a/c for Switzerland).