Telex
Anticensorship in the Network Infrastructure: Watch out for Telex.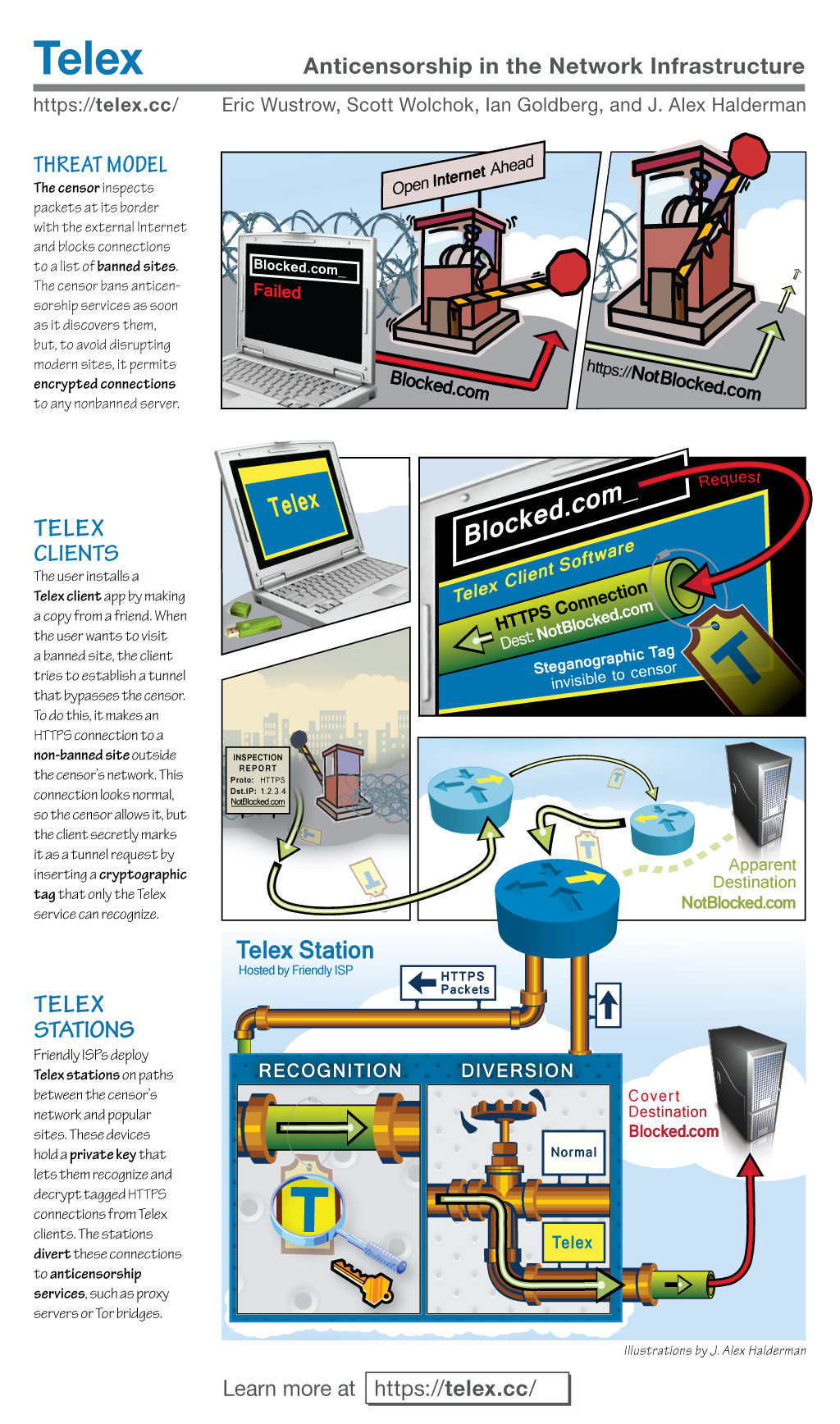
Telex is a new approach to circumventing Internet censorship that is intended to help citizens of repressive governments freely access online services and information. The main idea behind Telex is to place anticensorship technology into the Internet’s core network infrastructure, through cooperation from large ISPs. Telex is markedly different from past anticensorship systems, making it easy to distribute and very difficult to detect and block.
What makes Telex different from previous approaches:
- Telex operates in the network infrastructure — at any ISP between the censor’s network and non-blocked portions of the Internet — rather than at network end points. This approach, which we call “end-to-middle” proxying, can make the system robust against countermeasures (such as blocking) by the censor.
- Telex focuses on avoiding detection by the censor. That is, it allows a user to circumvent a censor without alerting the censor to the act of circumvention. It complements services like Tor (which focus on hiding with whom the user is attempting to communicate instead of that that the user is attempting to have an anonymous conversation) rather than replacing them.
- Telex employs a form of deep-packet inspection — a technology sometimes used to censor communication — and repurposes it to circumvent censorship.
- Other systems require distributing secrets, such as encryption keys or IP addresses, to individual users. If the censor discovers these secrets, it can block the system. With Telex, there are no secrets that need to be communicated to users in advance, only the publicly available client software.
- Telex can provide a state-level response to state-level censorship. We envision that friendly countries would create incentives for ISPs to deploy Telex.